ABSTRACT
The Internet of Things (IoT) is undeniably transforming the way that organizations communicate and organize everyday businesses and industrial procedures. Its adoption has proven well suited for sectors that manage a large number of assets and coordinate complex and distributed processes. This survey analyzes the great potential for applying IoT technologies (i.e., data-driven applications or embedded automation and intelligent adaptive systems) to revolutionize modern warfare and provide benefits similar to those in industry.
It identifies scenarios where Defense and Public Safety (PS) could leverage better commercial IoT capabilities to deliver greater survivability to the warfighter or first responders, while reducing costs and increasing operation efficiency and effectiveness. This article reviews the main tactical requirements and the architecture, examining gaps and shortcomings in existing IoT systems across the military field and mission-critical scenarios. The review characterizes the open challenges for a broad deployment and presents a research roadmap for enabling an affordable IoT for defense and PS.
COMPELLING COTS IOT APPLICATIONS
The introduction of the Network-Centric Warfare (NCW) paradigm transformed traditional military approaches by reversing the policy of expanded communication gateways, and by connecting battlefield assets back to headquarters. Through sharing data between both legacy assets and new deployments, this military vision creates advantages through force projection and secure timely exchanges of information between users. The NCW paradigm integrates three domains: the physical domain, generating data where events happen and operations are conducted; the information domain, in which data are transmitted and stored; and the cognitive domain, in which data are processed and analyzed supporting decision-making. The three domains of NCW translate directly into the foundations of today’s commercial IoT.
TARGET SCENARIOS FOR MISSION-CRITICAL IOT

Figure 4. Soldiers of today and the future
Other examples are Cubic’s I-MILES (Instrumented-multiple Integrated Laser Engagement System) training solutions which simulate combat using lasers and visual augmentation. They use connectivity, computer modeling and neuroscience-based learning tools to provide a more comprehensive real-time training experience. The solutions simulate artillery fire and provide a battle effect simulator, which include explosive devices like land mines, booby traps, and pyrotechnics. The previously referred applications, and others yet-to-be imagined, could be part of the equipment of the soldiers of the future. A likely evolution of such equipment can be seen in Figure 4.
OPERATIONAL REQUIREMENTS
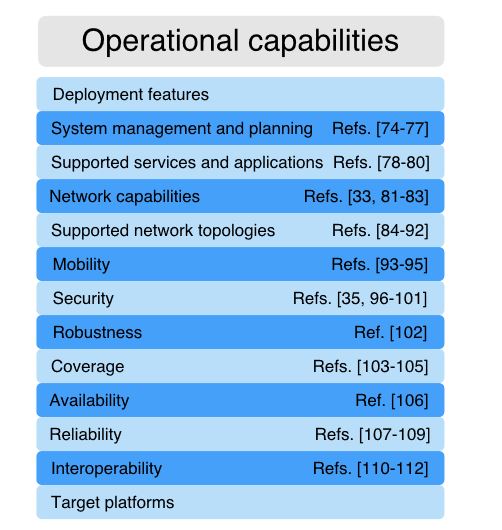
Figure 5. Operational Capabilities assessed to cover mission-critical scenarios
The military has unique operational requirements. Security, safety, robustness, inter-operability challenges, as well as bureaucratic and cultural barriers, stand in the way of the broad adoption of new IoT applications. In this Section a set of operational requirements grouped by capabilities (represented in Figure 5) are assessed in order to cover the scenarios previously discussed.One of the biggest constraints in a battlefield environment is power consumption. IoT devices are likely to be powered by batteries or solar power, and charged on-the-move from solar panels, trucks, or even by motion while walking.
In either case, they should last for extended periods of time (at least for the duration of the mission). Therefore, devices and sensors need to be power-efficient, and end-users have to use them appropriately. Likewise, it is not easy to recharge IoT devices periodically or swap out batteries in deployed devices. Even in the case of body-worn devices, it is impractical to expect soldiers to carry additional batteries on top of their current equipment.
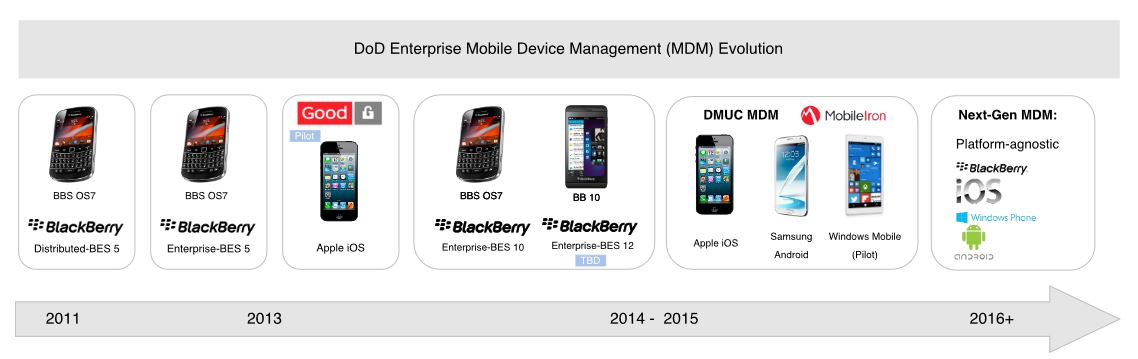
Figure 7. DoD Enterprise Mobile Devices Management (MDM) evolution
These devices, which are modified from COTS Samsung Galaxy Note II smart phones, provide access to the data-capable Rifleman radio. It aims to connect soldiers in the field with a range of apps, such as Blue Force Tracking, 3-D maps, or an application that shows details on profiles of high-value targets. The devices run an NSA-approved version of the Android operating system, and plan to include applications such as foreign language translation. These programs have been piloted on a limited basis. Broader deployment is hampered by the limited usability, functionality and lack of connectivity. Other commercial devices can be seen in Figure 7.
BUILDING IOT FOR TACTICAL AND EMERGENCY ENVIRONMENTS
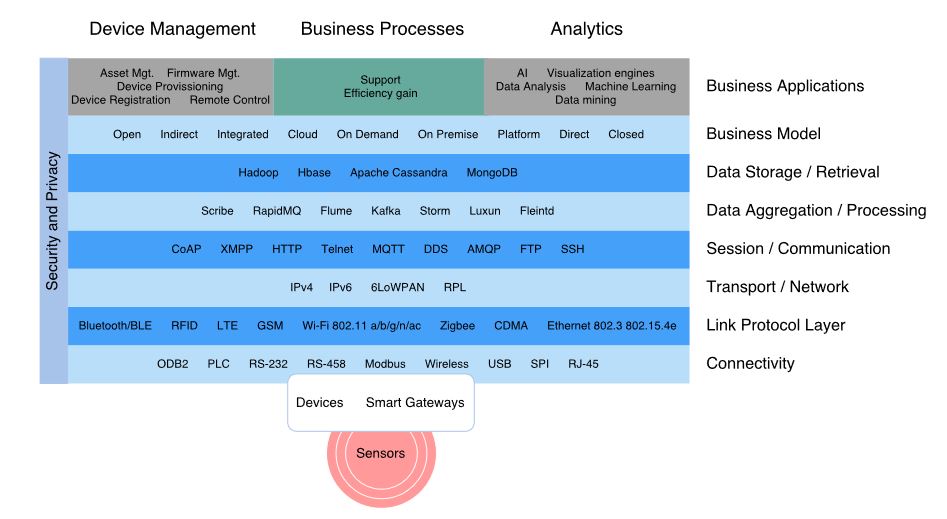
Figure 10. IoT landscape
In order to understand the complex adoption of IoT for defense, this section will briefly review the basics of IoT landscape (a graphical overview of the main elements can be seen in Figure 10) to support the requirements previously explained. First, it focuses on the architecture with an overview of the most important elements. Next, the section examines the main standardized protocols and technologies.
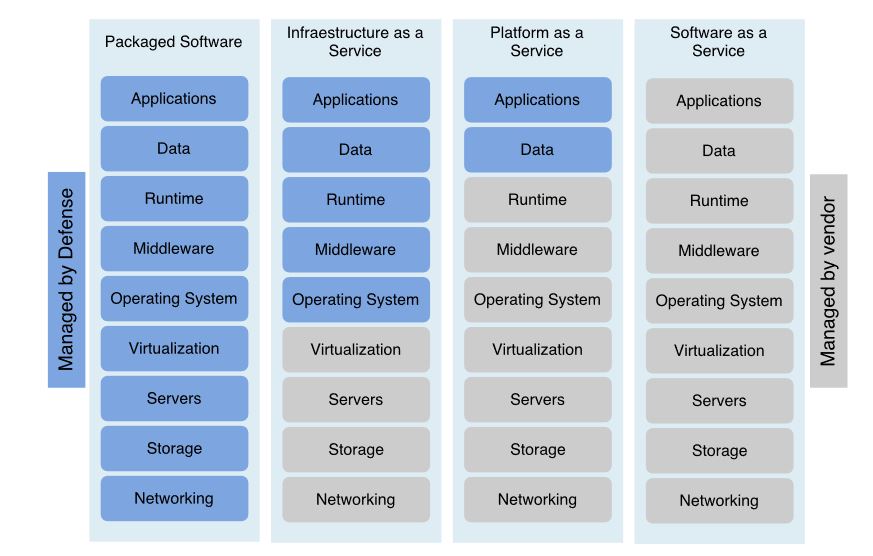
Figure 13. Cloud paradigms: security inheritance and risks
In term of resources, besides the powerful servers in data centers, a lot of smart devices around us offer computing capabilities that can be used to perform parallel IoT data analytic tasks. Instead of providing applications specific analytics, IoT needs a common big data analytic platform which can be delivered as a service to IoT applications. Such an analytic service should not impose a considerable overhead on the overall IoT ecosystem. The three most popular cloud paradigms are Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Their structure and corresponding security risks are represented in Figure 13.
MAIN CHALLENGES AND TECHNICAL LIMITATIONS
There are significant challenges in the development and deployment of existing and planned military IoT systems. Nowadays, only a small number of military systems leverage the full advantages of IoT. Ongoing NATO Research Task Group (RTG) Military Applications of Internet of Things (IST-147) is examining a number of critical issues identified by the recommendations from two previous exploratory team activities: IST-ET-076, ‘Internet of Military Things’ which examined topics relevant to the application of IoT technologies, and IST-ET-075, ’Integration of Sensors and Communication Networks’, which addressed networking issues.
The deployment of IoT-related technologies is in segregated vertical stovepipes making it difficult to secure them, and limiting the ability to communicate across systems and generate synergies from different data sources. Main defense concerns include the dependence of manual entry, the limited processing of data, the lack of automation, and the fragmented IT architecture.
CONCLUSIONS
This article examined how the defense industry can leverage the opportunities created by the commercial IoT transformation. Main topics relevant to the application of IoT concepts to the military and public safety domain were explained. In order to perform the study, we propose significant scenarios such as: C4ISR, fire-control systems, logistics (fleet management and individual supplies), smart cities operations, personal sensing, soldier healthcare and workforce training, collaborative and crowd sensing, energy management, and surveillance. The added value and the risk of applying IoT technologies in the selected scenarios were also assessed.
Based on the operational requirements, we proposed the architecture, technologies and protocols that address the most significant capabilities. Commercial IoT still faces many challenges, such as standardization, scalability, interoperability, and security. Researchers working on defense have to cope with additional issues posed by tactical environments, and the nature of operations and networks. There are three main differences between Defense/PS IoT and COTS IoT: the complexity of the deployments, the resource constraints (basically the ones related to power consumption and communications), and the use of centralized cloud-based architectures.
Organic transitions such as supply chain management and logistics will naturally migrate to mission-critical environments. Beyond the earliest military IoT innovations, complex battlefields will require additional research advances to address the specific demands. In addition to addressing various technical challenges, this work identified vital areas of further research in the 2016–2020 time frame. Moreover, battlefield domains that closely integrate human cognitive processes will require new or extensions of current theories of information that scale into deterministic situations.
Source: Deloitte University
Authors: Paula Fraga-lamas | Tiago M. Fernandez-Carames | Manuel Suarez-Albela | Luis Castedo | Miguel Gonzalez-lopez
>> IoT based Big Data and Cloud Computing Projects for B.E/B.Tech Students
>> IoT based Networking Projects for Engineering Students
>> IoT Environmental Monitoring System for Smart Cities Projects for Students
>> IoT Software Projects for Final Year Students