ABSTRACT
This paper presents a dominant channel occupancy (DCO) mechanism for the Wi-Fi backscatter uplink in the industrial Internet of things (IIoT). The DCO provides high-priority channel access and reliable burst transmission to the Wi-Fi backscatter devices, thereby enabling the Wi-Fi backscatter tag to deliver its tag information to the Wi-Fi reader without interference from neighboring legacy Wi-Fi devices to guarantee the timeliness and reliability of the IIoT system. For the former, we consider three types of medium access control (MAC) configurations: “carrier sense multiple access with collision avoidance (CSMA/CA) starting with short inter-frame space (SIFS)”, “freezing of the backoff period”, and “reduced CWmin.”.
In addition, the DCO uses the SIFS between burst packets to guarantee reliable burst transmission. To verify the effectiveness of DCO and determine a proper value for MAC parameters, we conduct experimental simulations under IEEE 802.11n PHY/MAC environments. The simulation results show that the reduced CWmin has the most significant effect on the channel occupancy. The Wi-Fi backscatter devices achieve much higher throughput than the separate cases when two or more configurations are used simultaneously. Moreover, the results exhibit that the use of SIFS between consecutive packets supports reliable burst transmission regardless of the transmission of the legacy Wi-Fi devices in the vicinity.
Wi-Fi Backscatter Uplink Communication
Figure 1 illustrates the architecture and operation of Wi-Fi backscatter uplink communication. As shown in Figure 1a, the Wi-Fi backscatter includes three types of devices: the Wi-Fi reader, Wi-Fi helper, and Wi-Fi backscatter tag, which are the mobile device, Wi-Fi AP, and RF-powered device, respectively. For uplink communication, the Wi-Fi backscatter tag transmits its tag information to a Wi-Fi reader by either reflecting or not reflecting a Wi-Fi helper signal. Figure 1b shows the operation of Wi-Fi backscatter uplink communication.
Design of the DCO
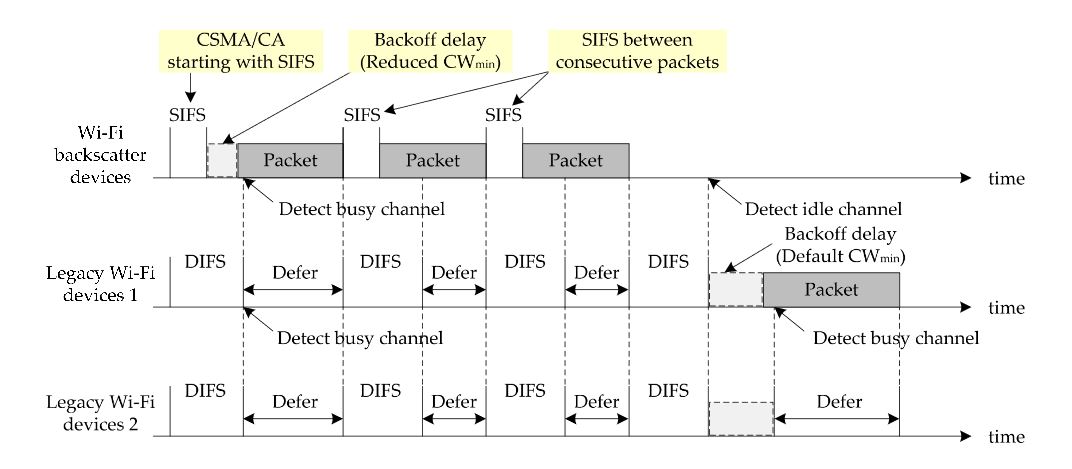
Figure 3. Example of burst transmission of DCO
Figure 3 shows an operational example of the burst transmission of Wi-Fi backscatter devices running DCO. In the example, a pair of Wi-Fi backscatter devices and two pairs of neighboring legacy Wi-Fi devices are assumed. The Wi-Fi backscatter devices employ DCO and have three packets for burst transmission. On the other hand, the legacy Wi-Fi devices use the CSMA/CA mechanism and have one packet to transmit. In the figure, one of the Wi-Fi backscatter devices transmits the packet earlier than the others since it uses “CSMA/CA starting with SIFS” and “reduced CWmin”. Due to the transmission of the Wi-Fi backscatter devices, the legacy Wi-Fi devices detect a busy channel after DIFS and defer their transmission until the end of the transmission.
PERFORMANCE EVALUATION
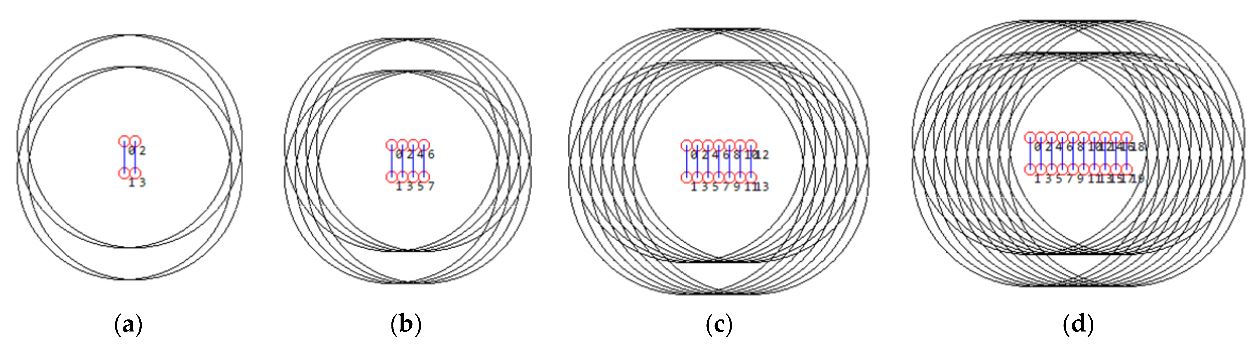
Figure 4. Examples of network topology: (a) four devices; (b) eight devices; (c) 14 devices; and (d) 20 devices
Figure 4 shows examples of the network topology with different numbers of devices. All devices are deployed in a 100 × 100 m2 region and have the same interference range. We consider a pair of devices per transmission and set the Tx devices to transmit the packets consecutively. Multiple pairs of devices are deployed in the simulation region; one of the pairs is set to the Wi‐Fi backscatter devices, and others are set to the legacy Wi‐Fi devices.
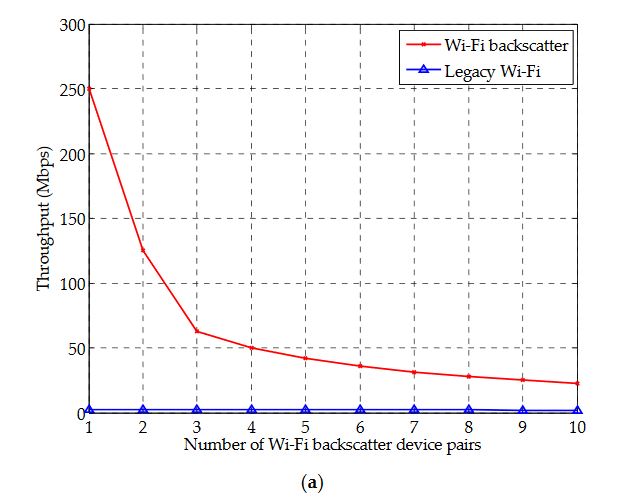
Figure 10. Cont
Figure 10 shows the throughput variation and the number of consecutive packet transmissions for multiple pairs of Wi-Fi backscatter devices. In the simulation, 20 pairs of devices are deployed in total; the number of Wi-Fi backscatter device pairs started from one and rose to 10 in single-step increments, and the rest is set to the pairs of legacy Wi-Fi devices. All MAC configurations are employed for the pairs of Wi-Fi backscatter devices, and CWmin is set to three. In addition, the number of consecutive packets for burst transmission is set to 100.
CONCLUSIONS
This paper presents DCO to guarantee the timeliness and reliability of the IIoT system. The DCO is designed to provide high-priority channel access and reliable burst transmission. For the former, three types of MAC configurations are considered: “CSMA/CA starting with SIFS”, “freezing of the backoff period”, and “reduced CWmin.” For the latter, we consider the SIFS between consecutive packets instead of DIFS. The simulation results show that the DCO can guarantee the dominant-channel occupancy of Wi-Fi backscatter devices regardless of the interference from other legacy Wi-Fi devices in the vicinity.
The CSMA/CA starting with SIFS and the freezing of the backoff period can improve the channel occupancy by 85% and 29%, respectively. The reduced CWmin is the most effective MAC configuration for the initial channel access in separate cases. When CWmin = 1, most of the shared wireless channel is occupied by Wi-Fi backscatter devices. Moreover, the Wi-Fi backscatter devices achieve much higher channel occupancy than the separate cases when multiple MAC configurations are used compositely. If all of the MAC configurations with CWmin = 1 are employed for the Wi-Fi backscatter devices, they always have the highest priority for channel access.
In the case where the Wi-Fi backscatter devices use the SIFS between consecutive packets, they transmit the packets successively regardless of the transmissions of the legacy Wi-Fi devices in the vicinity. This paper focuses on the design of DCO and performance evaluation via experimental simulation. Future work will be directed towards implementing DCO using available Wi-Fi open source device drivers, since this requires the additional low MAC development of a Wi-Fi helper. In particular, we will evaluate and verify the feasibility of DCO in real IIoT environments through such an implementation.
Source: Hallym University
Authors: Jung-hyok Kwon | Hwi-ho Lee | Yongseok Lim | Eui-jik Kim
>> More Wireless Hacking Projects for Wi-fi Enthusiasts for Engineering Students