ABSTRACT
Recent technological advancements allowed widening the applicability scope of the RFID (Radio Frequency Identification) technology from item identification to sensor-enabled computation platforms. This feature, added to the native radio energy-harvesting capability and the extremely low power consumption, has attracted the interest of research and industrial communities and pushed them to include the RFID technology into a global network of interconnected objects, as envisaged by the Internet of Things paradigm. In the last few years, standardization bodies have made significant efforts to design lightweight approaches, such as CoAP (Constrained Application Protocol), to efficiently manage resource-constrained nodes by using traditional web interfaces; nevertheless, RFID integration is not addressed yet.
In this paper, we propose a CoAP-compliant solution where RFID tags, behaving as virtual CoAP servers, are directly accessible by remote CoAP clients via a reader, which acts as a CoAP proxy. A real testbed, addressing key aspects, such as tag addressing, discovery and management of CoAP requests via RFID operations, is deployed to validate the feasibility of the proposal. Experimental results show rapid response times: less than 60 ms are requested for resource retrieval, while from 80 to 360 ms for sending data to the RFID device, depending on the tag memory dimension.
RELATED WORKS AND RESEARCH BACKGROUND
This section addresses the state-of-the-art of the research activities conducted in the areas of interest for our research. We first focus on the RFID technology to provide detailed information about communication protocols standardized for both UHF readers and tags. Then, we thoroughly browse relevant literature works that introduce several schemes to enable resource retrieval of sensor-equipped RFID tags, in the absence of a standardized solution. Last, we introduce the solutions to access resources of constrained devices by adopting the so-called Web of Things paradigm. Attention is paid to the description of the CoAP protocol and to the core concepts to enable web interfaces for IoT nodes.
APPROACHES FOR RFID INCLUSION IN THE IOT
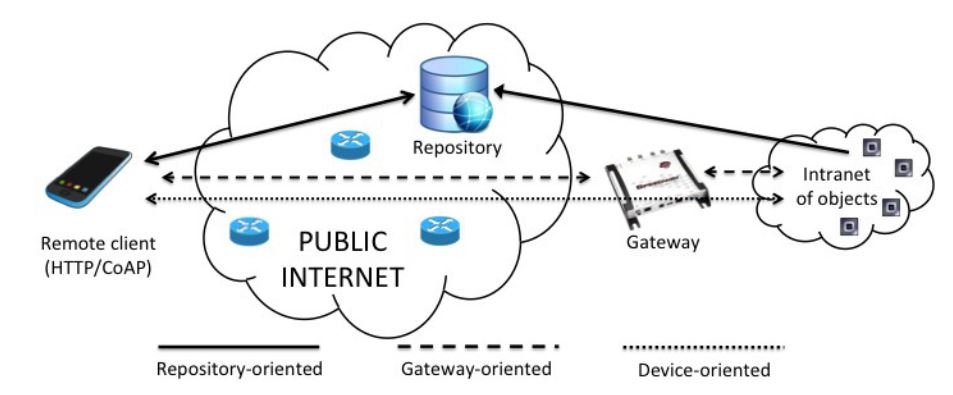
Figure 1. Representation of the three discussed approaches for RFID inclusion in the IoT
Figure 1 schematically depicts the three approaches for RFID inclusion in the IoT that will be discussed in the remainder of this paper. The first architecture envisages the use of repositories to store the information relevant to legacy RFID tags, i.e., “traditional” low-cost tags only equipped with user memory. When a user is interested in retrieving information about a device, he/she issues a request to the appropriate repository, which typically exposes the devices resources through web services.
THE PROPOSED ARCHITECTURE FOR RFID INCLUSION IN THE IOT
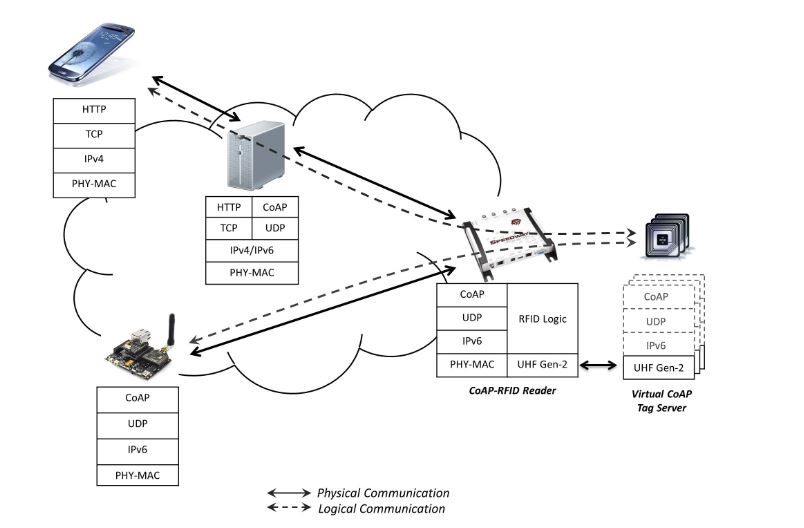
Figure 2. Protocol stack
Tags do not terminate CoAP traffic directly, but communicate with the reader, which transparently represents the tag (physical object) for a remote client, since it intercepts all of the requests sent to the URIs of tags and replies on their behalf. In this way, we adhere to a device-oriented integration philosophy, as described in the previous section. The reader also acts as a Resource Directory (RD) for the managed tags; it stores the description of tags resources and allows remote lookup for these resources.
Thus, tags inventory can be performed by using a CoAP logic, i.e., by simply requesting of the RD the addresses of all of the nodes in a specific domain. Emulating web service interfaces between CoAP endpoints guarantees the respect of the basic principle of end-to-end connectivity, thus enabling communications between constrained nodes with different technologies. The use of specific HTTP-CoAP proxies enables access to tag resources also from HTTP clients and fosters the deployment of web applications (see Figure 2).
APPLICATION SCENARIOS: AN EXAMPLE
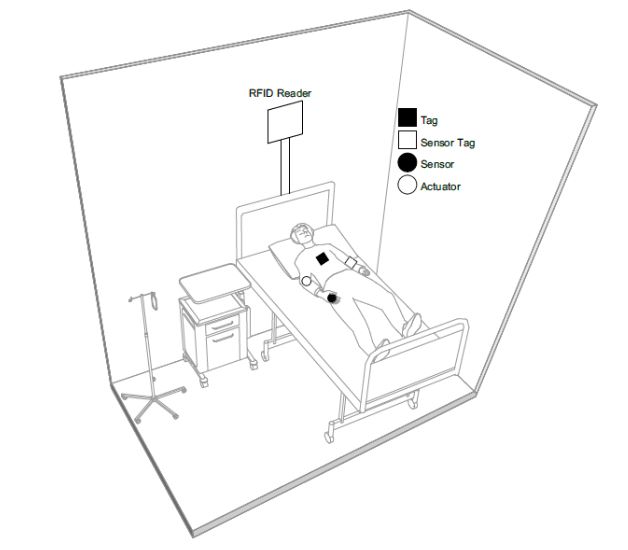
Figure 3. RFID-enabled IoT scenario
Among these, of particular interest is the personal smart health scenario, since the possibility to monitor the user health and activate remote assistance is gaining more and more attention due to both the rise in life expectation and the availability of a wide variety of increasingly inexpensive sensors. In such a scenario, RFID systems represent a key enabler because of the energy-autonomy and the low cost of battery-less tags that make them compatible with a widespread distribution and disposable applications. Figure 3 depicts a possible future scenario, wherein different kinds of resource-constrained nodes interact to implement a patient monitoring and support system.
IMPLEMENTATION
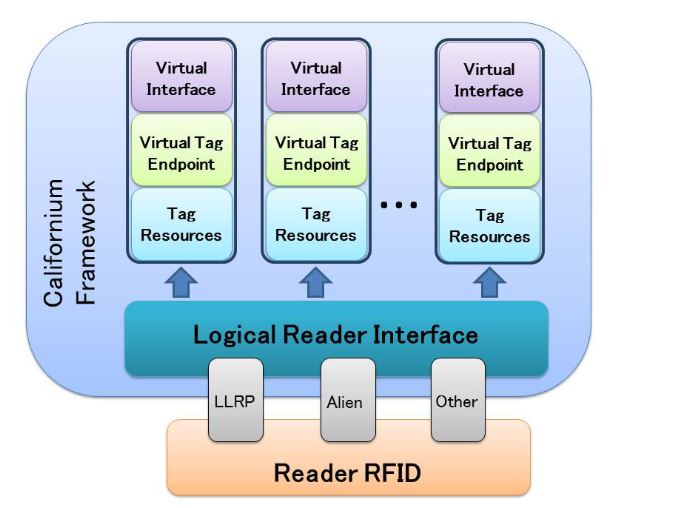
Figure 5. Architecture of the implemented “CoAP-RFID proxy reader”
Figure 5 illustrates the overall system architecture. First of all, we have extended Californium to support RFID operations, such as inventory, reading and writing. We provided a set of common APIs, defining a logical reader interface, that guarantee an abstraction layer from the communication interface of the RFID reader. In this way, our platform can be directly executed on a RFID reader (or on a server with a direct connection to the RFID reader), by implementing the appropriate protocol compliant with the logical reader interface. For instance, the RFID reader can be controlled by using the standardized LLRP protocol or vendor protocols.
TESTBED SETUP AND EXPERIMENTAL RESULTS
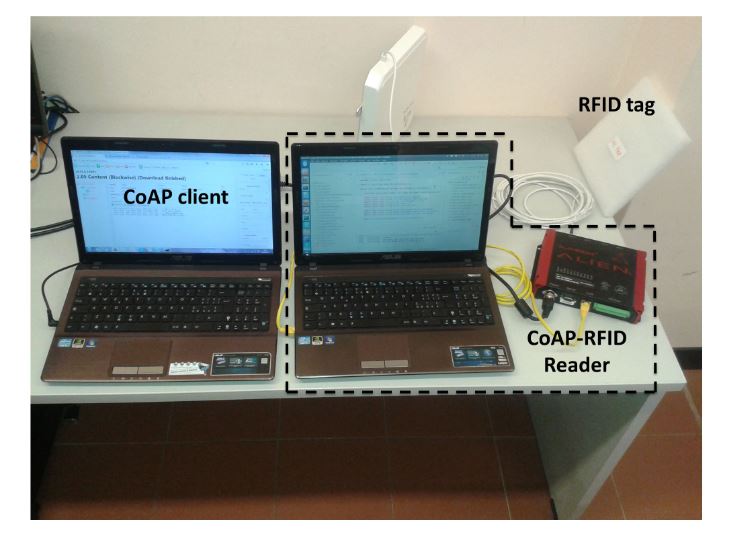
Figure 6. Testbed environment
Moreover, we use UHF Impinj Monza tags, equipped with an EEPROM user memory of 512 bits. The CoAP client is running on a different workstation with features analogous to the other laptop, with which it communicates via a wireless IEEE 802.11 connection. The testbed is outlined in Figure 6. We highlight that the used commercial UHF RFID tags present high reading and writing sensitivity, which allows for transmissions up to 5 to 10 m according to environmental conditions.
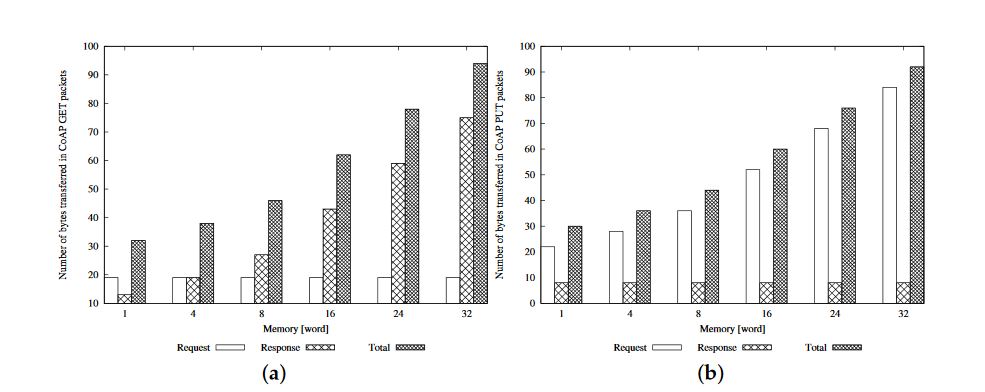
Figure 9. Amount of transferred bytes in CoAP: (a) GET; and (b) PUT packets
Finally, in Figure 9 , we plot the size of the packets at the CoAP level for GET and PUT operations, explicitly reporting the details of both request and response messages. The figures highlight that the total amount of transferred bytes is similar in the case of the GET and PUT operations, but Request and Response messages have different sizes in the two cases. In particular, the dimension of the Request message for a GET operation is constant (it contains only the header), while the size of the Response message increases when the dimension of the user memory grows (it carries the content of the user memory). These considerations can be inferred by looking at Figure 9 a. In the case of a PUT operation (see Figure 9 b), we have the opposite situation, since the value of the resource to be modified is transferred in the Request message while no payload is carried in the Response message.
CONCLUSIONS
In this paper, we have thoroughly discussed the issue of an efficient inclusion of the RFID technology in the IoT, by analyzing the pro and cons of different integration schemes. Accounting for the current capabilities of RFID technology, we have proposed a CoAP-compliant solution that allows one to directly access RFID tags (and related resources) via the reader. In the conceived architecture, the RFID reader works as a proxy for the managed tags, which act as virtual CoAP servers. We have accurately investigated the benefits of exploiting the proposed solution in a promising healthcare environment, by evaluating the interactions among smart health devices in such an environment. Then, we have implemented our proposal, by leveraging an open-source CoAP framework, and we have assessed the performance in a real scenario.
Source: University Mediterranea
Authors: Ivan Farris | Sara Pizzi | Antonella Molinaro | Antonio Iera
>> 200+ IoT Led Projects for Final Year Students
>> More Wireless Energy Projects for Engineering Students