ABSTRACT
This work considers the problem of attack-resilient sensor fusion in an autonomous system where multiple sensors measure the same physical variable. A malicious attacker may corrupt a subset of these sensors and send wrong measurements to the controller on their behalf, potentially compromising the safety of the system. We formalize the goals and constraints of such an attacker who also wants to avoid detection by the system. We argue that the attacker’s capabilities depend on the amount of information she has about the correct sensors’ measurements.
In the presence of a shared bus where messages are broadcast to all components connected to the network, the attacker may consider all other measurements before sending her own in order to achieve maximal impact. Consequently, we investigate effects of communication schedules on sensor fusion performance. We provide worst-and average-case results in support of the Ascending schedule, where sensors send their measurements in a fixed succession based on their precision, starting from the most precise sensors. Finally, we provide a case study to illustrate the use of this approach.
PROBLEM STATEMENT AND PRELIMINARIES
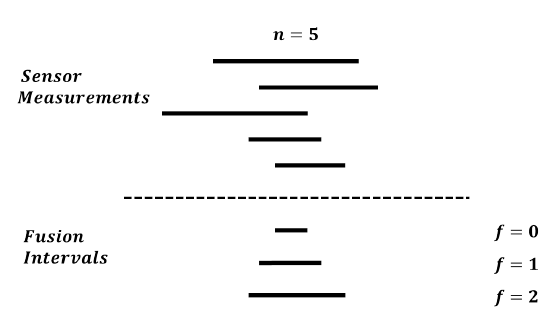
Fig. 1. Marzullo’s fusion interval for three values of f. Dashed horizontal
line separates sensor intervals from fusion intervals in all figures in this work.
The algorithm is illustrated in Fig. 1. When f = 0 and the system is confident that every interval is correct, the fusion interval is just the intersection of all intervals. When at most one sensor can be faulty (f = 1), the fusion interval is the convex hull of all points contained in at least four intervals. Similarly, when f = 2 the fusion interval contains the convex hull of all points that lie in at least three intervals. As shown in Fig. 1, as f increases so does the uncertainty represented as the size of the fusion interval.
ATTACK POLICY AND WORST-CASE ANALYSIS
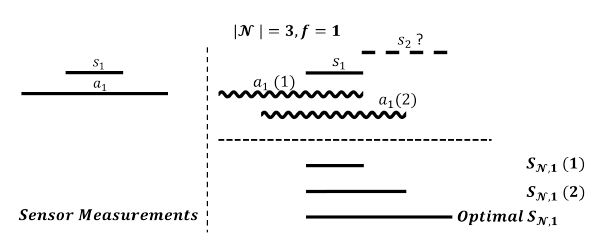
Fig. 2. An example showing that if attacker (sinusoid) has not seen all intervals then she has no policy that guarantees fusion interval is maximized.
Given placements of the correct intervals, an attack policy is optimal if the fusion interval has the same size as in the solution of problem. Thus, the policy described is optimal by definition.2 We argue, however, that in general there exists no optimal policy for the attacker if she is not aware of all correct intervals before sending hers.This is illustrated in Fig. 2.
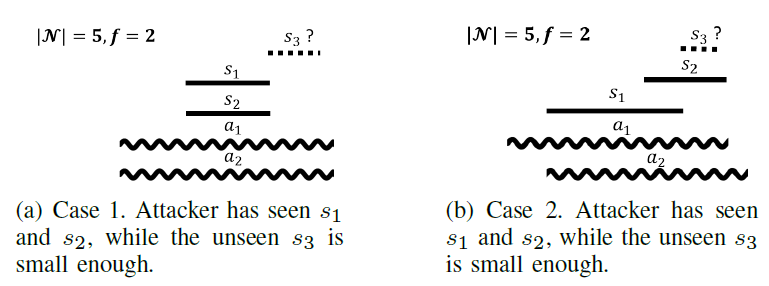
Fig. 3. Examples of the two cases of Theorem 1. Attacked intervals are indicated by sinusoids.
Fig. 3(a) illustrates this case. All seen correct intervals coincide, and the attacker’s intervals are large enough to guarantee that attacking on both sides will make sure all unseen intervals are included. Fig. 3(b) presents an example of this case. The unseen interval, s3, cannot change the largest and smallest points contained in at least one correct interval.
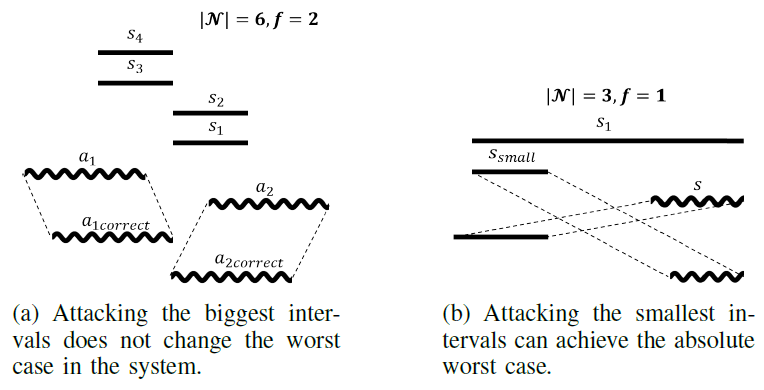
Fig. 4. Illustrations of Theorems 3 and 4.
Fig. 4(a) illustrates this theorem. Intervals a1 and a2 are under attack and both do not contain the true value, which is at the intersection of the other sensors. Fig. 4(b) gives an example the theorem. The worst-case for the setup can be achieved when s or ssmall is attacked. Theorems 3 and 4 suggest that the attacker can gain more power by corrupting the precise sensors as opposed to the imprecise.
SENSOR SCHEDULING FOR ATTACK-RESILIENT SENSOR FUSION

Fig. 5. Two examples that show that neither schedule is better in all situations. The first column shows the measurements by the sensors, including the attacked one. The other columns contain the intervals sent to the controller, and the corresponding fusion interval.
We first note that neither schedule is optimal in all scenarios. Theorem 1 suggests that it might be better for the attacker to see large intervals first. Fig. 5(a) illustrates an example where this is true. Fig. 5(b), however, shows that knowing the largest interval does not necessarily bring the attacker any useful information because she can only increase the fusion interval by overlapping with s1 and s2.

Fig. 6. LandShark vehicle.
The LandShark is commonly used in hostile environments to save injured people or carry other cargo. It has four sensors that estimate its speed – GPS, two encoders and a camera. The size of the GPS and camera intervals were determined empirically – the LandShark was driven in the open and largest deviations from actual speed were recorded for both the GPS and camera speed estimates. The encoders’ intervals were determined based on their manufacturer specification.
CONCLUSION
This work described a general sensor fusion algorithm for multiple sensors measuring the same physical value. We introduced security issues by formalizing an attack policy that tries to maximize the size of the fusion interval while staying undetected. Furthermore, we proposed a communication schedule, namely the Ascending schedule, that aims to minimize the attacker’s capabilities by either providing her with little information (sending at the beginning of the schedule) or little power (large intervals). We presented worst and average-case results that support our choice of schedule and validated our results in simulation and a case study. Since we assumed uncompromised sensors always provide correct measurements, an extension of this work will introduce random faults in addition to attacks.
Source: University of Pennsylvania
Authors: Radoslav Ivanov | Miroslav Pajic | Insup Lee