INTRODUCTION
Over the past decade, the design process in the automotive industry has gone through a period of significant changes. Modern vehicles present a complex interaction of a large number of embedded Electronic Control Units (ECUs), interacting with each other over different types of networks.
Furthermore, there is a current shift in vehicle architectures, from isolated control systems to more open automotive architectures that would introduce new services such as remote diagnostics and code updates, and vehicle-to-vehicle communication. However, this increasing set of functionalities, network interoperability, and system design complexity may introduce security vulnerabilities that are easily exploitable.
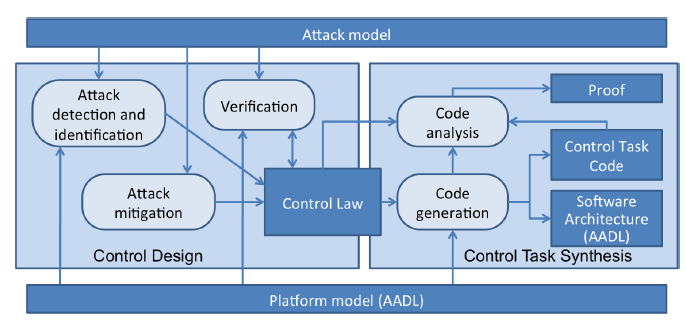
Figure 1: Overview of the approach.
The overview of the development framework is shown in Fig. 1. To protect against the set of attacks that is as extensive and diverse as possible, we combine control-level techniques and code-level techniques
ATTACK-RESILIENT CONTROL SCHEMES
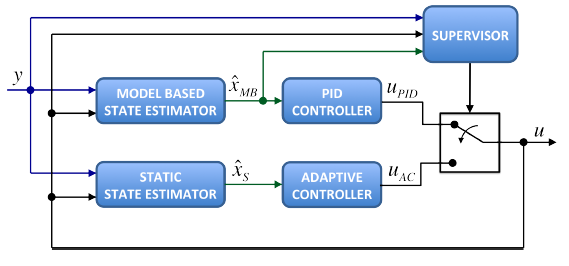
Figure 2: Diagram of the resilient controller.
Most of the existing schemes for attack detection and identification are based on the knowledge of the exact plant model. However, as the environmental conditions might affect some of the model parameters, we combine the resilient estimator with a controller scheme we have introduced, which is resilient to both attacks and limited perturbations in model parameters. Thus, the overall controller design (shown in Fig. 2) guarantees that in the event the model becomes inaccurate, we can maintain a minimum performance level for the closed-loop system.
SAFE CODE GENERATION
Existing methods for designing secure control systems do not offer coordinated control-level and code-level defenses. Tools like Matlab allow us to model control laws and generate code, but security properties of the generated code are not well studied. Our aim is to prove that behavior of the control algorithm is preserved by code generation and that no vulnerabilities are introduced in the process.
The code of control tasks is executed on top of the underlying communication and computation platform. Therefore, proofs of control code execution need to take properties of the platform into account. We plan to precisely specify the services provided by the platform and use these specifications in proof construction.
Source: University of Pennsylvania
Authors: Miroslav Pajic | Nicola Bezzo | James Weimer | Rajeev Alur | Rahul Mangharam | Nathan Michael | George J. Pappas | Oleg Sokolsky | Paulo Tabuada | Stephanie Weirich | Insup Lee
>> 200+ Matlab Projects based on Control System for Final Year Students
>> More Matlab Projects on Embedded Systems for Engineering Students