ABSTRACT
Recent measurements on radio spectrum usage have revealed the abundance of under- utilized bands of spectrum that belong to licensed users. This necessitated the paradigm shift from static to dynamic spectrum access (DSA) where secondary networks utilize un-used spectrum holes in the licensed bands without causing interference to the licensed user. However, wide scale deployment of these networks have been hinde red due to lack of knowledge of expected performance in realistic environments and lack of cost-effective solutions for implementing spectrum database systems. In this dissertation, we address some of the fundamental challenges on how to improve the performance of DSA networks in terms of connectivity and capacity. Apart from showing performance gains via simulation experiments, we designed, implemented, and deployed testbeds that achieve economics of scale.
We start by introducing network connectivity models and show that the well-established disk model does not hold true for interference-limited networks. Thus, we characterize connectivity based on signal to interference and noise ratio (SINR) and show that not all the deployed secondary nodes necessarily contribute towards the network’s connectivity. We identify such nodes and show that even-though a node might be communication-visible it can still be connectivity-invisible. The invisibility of such nodes is modeled using the concept of Poisson thinning. The connectivity-visible nodes are combined with the coverage shrinkage to develop the concept of effective density which is used to characterize the connectivity.
Further, we propose three techniques for connectivity maximization. We also show how traditional flooding techniques are not applicable under the SINR model and analyze the underlying causes for that. Moreover, we propose a modified version of probabilistic flooding that uses lower message overhead while accounting for the node outreach and interference. Next, we analyze the connectivity of multi-channel distributed networks and show how the invisibility that arises among the secondary nodes results in thinning which we characterize as channel abundance. We also capture the thinning that occurs due to the nodes’ interference. We study the effects of interference and channel abundance using Poisson thinning on the formation of a communication link between two nodes and also on the overall connectivity of the secondary network.
As for the capacity, we derive the bounds on the maximum achievable capacity of a randomly deployed secondary network with finite number of nodes in the presence of primary users since finding the exact capacity involves solving an optimization problem that shows in-scalability both in time and search space dimensionality. We speed up the optimization by reducing the optimizer’s search space. Next, we characterize the QoS that secondary users can expect. We do so by using vector quantization to partition the QoS space into finite number of regions each of which is represented by one QoS index. We argue that any operating condition of the system can be mapped to one of the precomputed QoS indices using a simple look-up in O log (N) time thus avoiding any cumbersome computation for QoS evaluation. We implement the QoS space on an 8-bit microcontroller and show how the mathematically intensive operations can be computed in a shorter time.
To demonstrate that there could be low cost solutions that scale, we present and implement an architecture that enables dynamic spectrum access for any type of network ranging from IoT to cellular. The three main components of this architecture are the RSSI sensing network, the DSA server, and the service engine. We use the concept of modular design in these components which allows transparency between them, scalability, and ease of maintenance and upgrade in a plug-n-play manner, without requiring any changes to the other components.
Moreover, we provide a blueprint on how to use off-the-shelf commercially available software configurable RF chips to build low cost spectrum sensors. Using testbed experiments, we demonstrate the efficiency of the proposed architecture by comparing its performance to that of a legacy system. We show the benefits in terms of resilience to jamming, channel relinquishment on primary arrival, and best channel determination and allocation. We also show the performance gains in terms of frame error rater and spectral efficiency.
RELATED WORK
In this chapter, we discuss the literature that is most relevant to this dissertation. We divide the discussion into,
- Connectivity
- Capacity of Distributed Wireless Networks
- DSA System Implementations
Connectivity of Distributed Wireless Networks
There is a rich literature with classical results for connectivity of both homogeneous and heterogeneous networks under both the Boolean model and the SINR model. Meester and Roy in were the first to show the percolation condition for continuum networks under the Boolean model is λ > λc, where λ is the deployment density and λc is some critical density.
CONNECTIVITY OF DSA NETWORKS
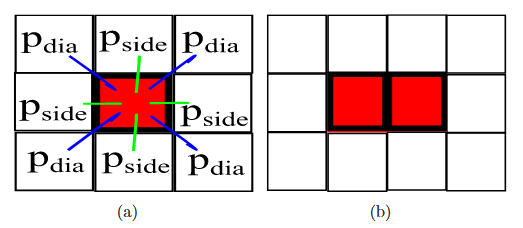
Figure 3.4 Illustration for pside and pdia. a) Isolated component within 1 square; b) Isolated component within 2 squares
The calculation of this probability is more involved. Since combinatorial counting algorithms in square lattice have been well-studied, we consider squares of siders. For each such square, we define 8 neighboring squares 4 on each side and 4 along the corners (or,diagonals). We define the no-crossing probability as the probability of having no successful communication between nodes in the neighboring squares due to interference. Two types of no-crossing probabilities arise: pside for no side crossing and pdia for no diagonal crossing.
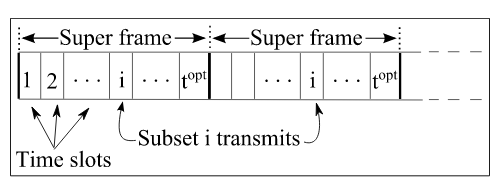
Figure 3.10 TDMA super-frame
We point out that, although the connectivity that results with topt is the best connectivity compared to the ones obtained with the other values of t, the connectivity obtained under topt opt is still suboptimal as the allocation is random and does not account for the nodes’ locations. However it does not require any priori knowledge among the nodes making this scheme easy to implement.
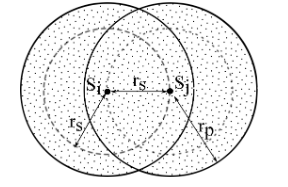
Figure 3.19 Area A in terms of the secondary and primary coverage zones
Consider two secondary nodes Si and Sj which are in range of each other and using some channel k as shown in Fig.3.19. Any primary user using channel k that comes within rp of Si or Sj will disrupt communications between Si and Sj. Thus, the shaded region in Fig.3.19, referred to as area A, must be void of primary users using channel k.
CAPACITY OF FINITE DSA NETWORKS
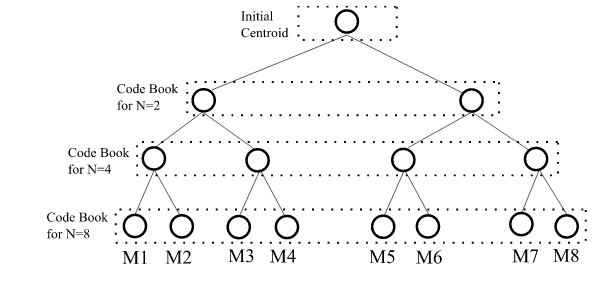
Figure 4.9 Codebook storage and lookup
Figure 4.9 gives an example of a TSVQ for N=8 with the intermediate code books of size 2 and 4 are also stored for the purpose of search. The final 8 code words are marked as M1 through M8. of size 8. Of course, the process of storing the intermediate code books is recursive which can generate code book of any size with is an exponent of 2.
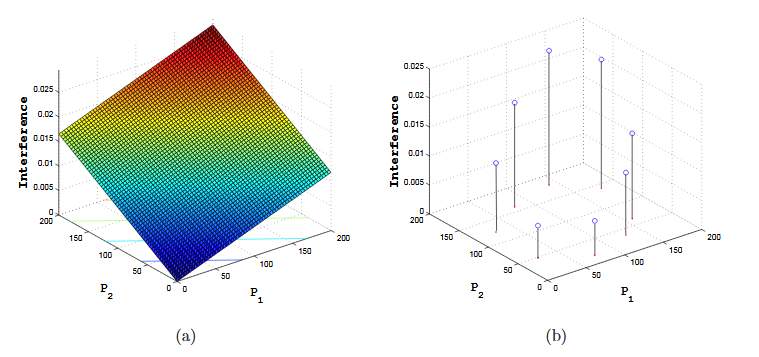
Figure 4.15 (a) Interference space of the primary, (b) Partitions of the interference space with their centroids
Let us consider a primary receiver located at (0,0) and two secondary transmitters at distances of 110 and 130 Meters respectively. The transmit power ranges from 0 to 200 mW. For each instance of P, we plot the corresponding interference at the primary for all values of P1 and P2 creating the Interference Space as shown in Fig.4.15(a).
Following the same approach in Section V (in creating the centroids for the capacity), we partition the space into 8 regions and find the 8 centroids as shown in Fig.4.15(b). These 8 centroids will be used to map the new values of P to find the expected interference on the primary.
DESIGN AND IMPLEMENTATION OF LOW COST DSA SYSTEM
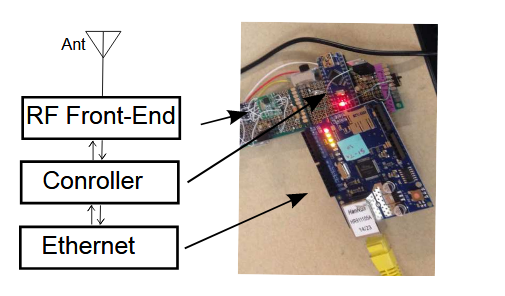
Figure 5.2 Block diagram of sensor node (left) with correspondence to an implemented unit (right)
A spectrum sensor unit/node primarily consists of two main components: the RF-front end and the controller. Depending on how the senor would be connected to the rest of the network, there could an additional Ethernet interface. A block diagram along with what has been actually implemented is shown in Fig.5.2. We emphasize that the design is not based on any specific component. These components are treated as generic building blocks. Our goal is to provide a guideline on how to capitalize on the off-the-shelf SCRF chips and controllers for making low-cost spectrum sensors.
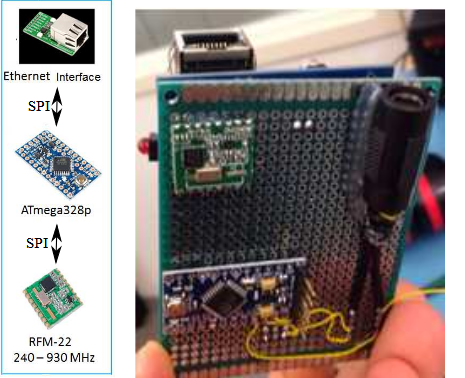
Figure 5.5 (a) Components for Type-1 sensor; (b) Assembled Type -1 sensor
Type-1 sensor is meant to detect sub-GHz frequencies. All the components were low cost off-the-shelf devices the total cost of which was less than $10. The individual components are shown in Fig.5.5(a) while the assembled one is shown in Fig.5.5(b).
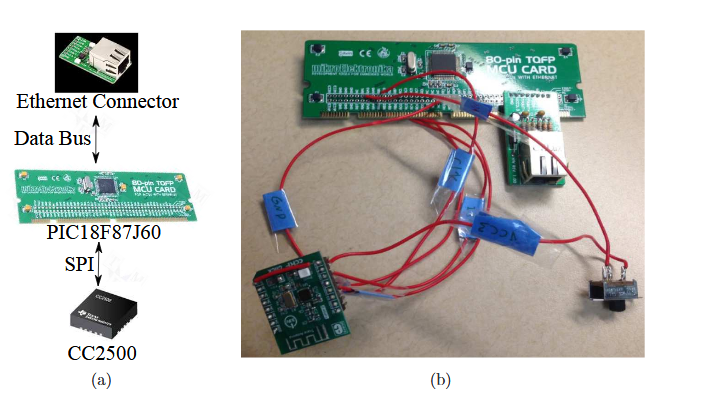
Figure 5.6 (a) Components for Type-2 sensor; (b) Assembled Type -2 sensor
Type-2 sensor is meant to detect the 2.4 GHz ISM band. Again, all components were off-the-shelf with the total cost being less than $10. The components are shown in Fig.5.6(a) while the assembled sensor is shown in Fig.5.6(b).
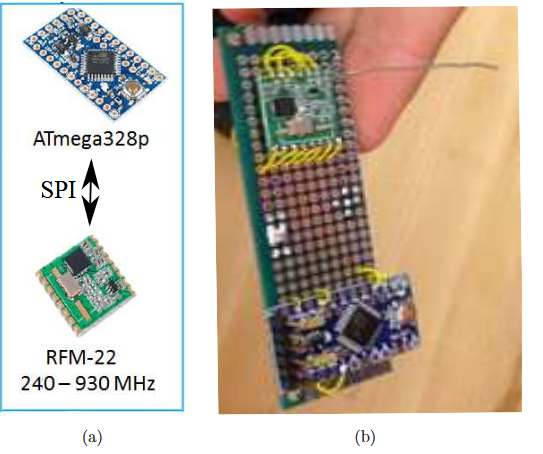
Figure 5.10 (a) Components for wireless sensor; (b) Assembled wire less sensor
The components of a wireless node are shown in Fig.5.10(a) while an assembled wireless sensor is shown in Fig.5 .10(b).
SIMULATION MODEL AND RESULTS
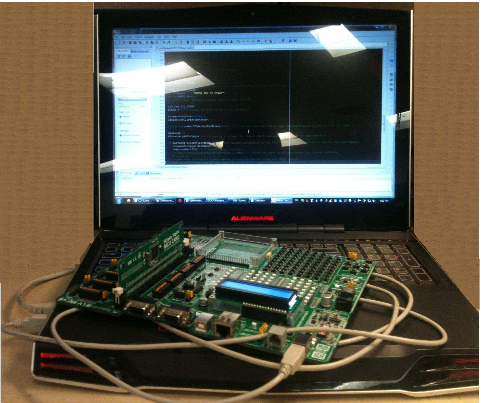
We implement VQ on two 8-bit devices: PIC18F87J60 and PIC16F877A, the former is running on a crystal oscillator of 25 MHz while the latter is running on a crystal oscillator of 8 MHz. Fig 6.26 shows the microcontroller development board that was used to in this work along with the PIC18F87J60 and the software development tools.
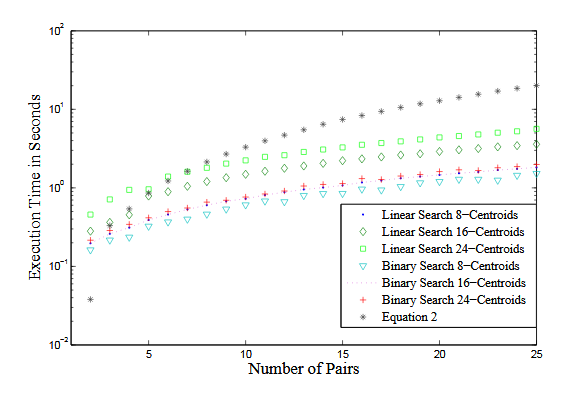
Figure 6.27 Time for computing Eqn.4.33 vs. look-up time for PIC16F877A
The results are shown in Fig.6.27. It can be seen that as K increases the time needed to compute the capacity equation grows almost exponential. As expected, the time needed for linear search scaled linearly as the number of centroids increased. This is because the number of computations increased linearly with the number of centroids i.e., the time needed for computing 16 centroids is twice the time needed for the 8 centroids. For the 24 centroids, it is 3 times the time of the 8 centroids.
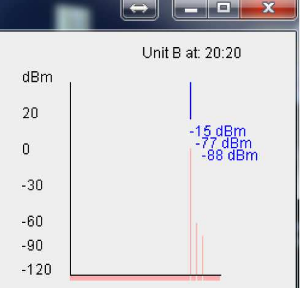
Figure 6.30 RSSI measurements at location-B for 900 MHz, 905 MHz, and 910 MHz, with the best channel being 910 MHz.
Fig.6.30 shows an instantaneous RSSI in dBm for 900 MHz, 905 MHz and 910 MHz at a particular location (namely, location-B). During that time, any request for a channel in the vicinity of location-B would be recommended to use the 910 MHz channel since it has the lowest RSSI (i.e.,-80 dBm) among the 3 channels. To induce controlled interference and mimic the primary users, we built two software configurable jammers using RFM22 transceivers as the front-end and ATmega328p as the controller.
CONCLUSIONS
This dissertation addresses some fundamental theoretical aspects on how to optimize connectivity and capacity of DSA networks, it also presents a low-cost yet effective architecture to solve the cost scalability problem that is hindering the wide scale deployment of such networks. With respect to connectivity, we found the conditions under which the giant component emerges in the secondary network. This is achieved by linking percolation from the Boolean model with the concept of effective density under the SINR model where we identified and excluded the nodes that are invisible to the giant component.
We utilized the concept of effective density to maximize the secondary network connectivity using three different approaches. We also studied the performance of flooding and traditional flooding under the SINR model and analyzed the sources of their performance degradation. Then we employed our findings on connectivity and proposed a modified probabilistic flooding technique which outperformed the popular techniques in terms of lower message overhead and the node outreach. We also analyzed the connectivity of multi-channel distributed networks and showed the individual as well as the combined effects of the scanning limitations,interference, primary users, and the existence of multi-channels on the resultant network connectivity.
The theoretical findings were supported by the simulation experiments which showed correspondence between the theoretical and practical results. As for the capacity, we derived the bounds on the capacity of a finite and randomly deployed secondary network in the presence of the primary users. Using dimensionality reduction, we sped up the constrained non-convex optimization problem. Then we showed how to quickly evaluate the resultant power vector using K-means clustering. We gauged the performance of our technique by running it on 8-bit microcontrollers and comparing the execution time vs. the traditional approach of evaluating a QoS metric. The results showed that our technique performed the evaluation in a shorter time.
Source: University of Central Florida
Author: Osama Al-tameemi
>> Top IoT Projects using Microcontroller for Engineering Students
>> 200+ IoT Led Projects for Final Year Students
>> IoT Software Projects for Final Year Students
>> More Wireless Sensor Networks Projects Abstract for Engineering Students