ABSTRACT
A logger in the cloud capable of keeping a secure, time-synchronized and tamper-evident log of medical device and patient information allows efficient forensic analysis in cases of adverse events or attacks on interoperable medical devices. A secure logger as such must meet requirements of confidentiality and integrity of message logs and provide tamper-detection and tamper-evidence.
In this paper, we propose a design for such a cloud-based secure logger using the Intel Software Guard Extensions (SGX) and the Trusted Platform Module (TPM). The proposed logger receives medical device information from a dongle attached to a medical device. The logger relies on SGX, TPM and standard encryption to maintain a secure communication channel even on an untrusted network and operating system. We also show that the logger is resilient against different kinds of attacks such as Replay attacks, Injection attacks and Eavesdropping attacks.
PROBLEM STATEMENT
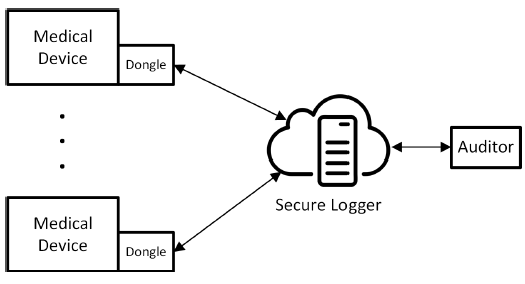
Fig. 1: A high-level overview of the logger.
As discussed in the previous section, our goal is to design a secure logger in the cloud for medical devices. In particular, we aim to develop a centralized logger that gets medical device and patient information from a dongle attached to each medical device. The data that it receives is stored as secure logs and can be later retrieved by an auditor for verification and analysis of tamper. Figure 1 illustrates a high-level overview of the logger’s environment.
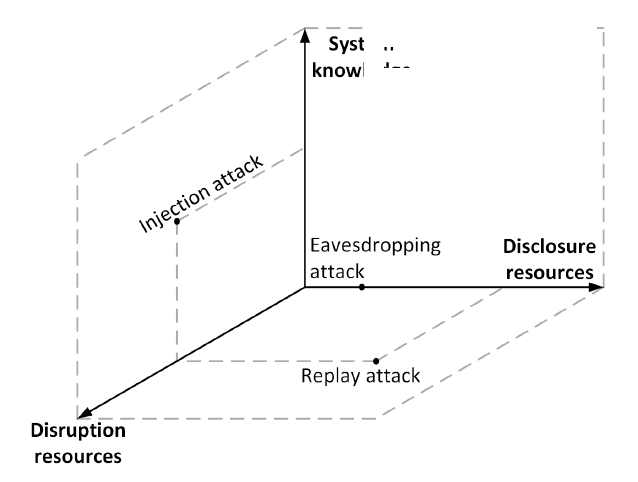
Fig. 2: Secure logger attack space.
We now explore the attack scenarios that a cloud based logger needs to defend against to meet these requirements. We illustrate the possible attack scenarios for our work in Figure 2 using the three dimensional attack space proposed by Teixeira et al. that comprises of the adversary’s system model knowledge, its disruption resources and disclosure resources.
DESIGN OF THE CLOUD-BASED SECURE LOGGER
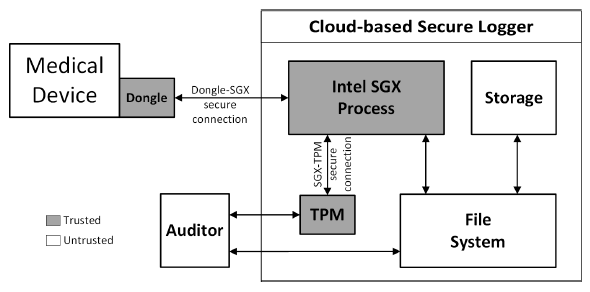
Fig. 3: Design architecture of the logger.
In the remaining part of this section, we first describe various components of our design presented in Figure 3 and discuss the functionality of each component. We then propose proper usage of these components to establish secure communication channels to defend against the attack scenarios previously discussed.
OPERATION OF THE CLOUD-BASED SECURE LOGGER
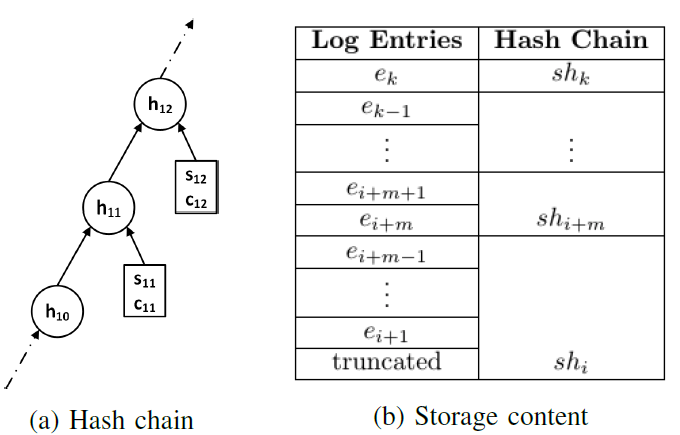
Fig. 4: A sample hash chain and content in logger storage. Hash shi can be used to recompute hash chain from ei + 1.
In practice, storing all the signed hash values is not required: given shi; shj where i < j, the hash chain from i to j can be re-computed to verify the integrity of the log. Therefore, we maintain a constant m indicating that the logger only stores signed hash value shi for every m log entries (ei+1; ei+2; :::; ei+m). When the log storage is full and there is a need for log truncation to prevent log overflow, we can safely remove shi and all the log entries from ei+1 to ei+m. Given shi+m, we are still able to re-compute the hash chain from ei+m+1 to the latest log entry as illustrated in Figure 4.
DISCUSSION OF SECURITY GUARANTEES
We described the requirements for a secure logger in the cloud as: confidentiality and integrity of transmitted and stored data, tamper-detection and tamper-evidence. In this section, we discuss how we ensure that the design meets the requirements under each attack scenarios.
- Eavesdropping Attack
- Injection Attack
- Replay Attack
Limitations
Our logging system is designed to make tampering of data detectable and thus, it detects and raises alarms when messages are altered. However, any behaviour that does not lead to altering of messages is not detected. For instance, when the logger does not get a reply from the dongle, it does not know if the dongle is under attack or just under normal shut-down. In addition, we protect the integrity of the information received by the dongle, but cannot guarantee the correctness of what it receives. Addressing these limitations are outside the scope of this paper. However, we do plan to explore and address these limitations in the future.
CONCLUSION
In this paper, we have described a secure logging system that provides tamper-evidence to message logs that it receives from medical devices on a network. We leverage the use of trusted hardware in an untrusted network to design such a secure logger. The design guarantees that attacks attempting to modify or delete logs are detected.
This project is a first attempt at mitigating cyber threats to medical devices with their imminent increase in interoperability with other devices on a hospital network. This is an ongoing project and the next step is to implement our design on a simulated ICE environment. Then, we will experiment on a small part of the local hospital network. Furthermore, we also aim to extend the attack space by looking at attacks like Denial of Service in more detail. Finally, we plan to explore the Data Distribution Service (DDS) middleware for efficient data delivery and security guarantees for our logger.
Source: University of Pennsylvania
Authors: Hung Nguyen | Bipeen Acharya | Radoslav Ivanov | Andreas Haeberlen | Linh T.X. Phan | Oleg Sokolsky | Jesse Walker | James Weimer | C. William Hanson III | Insup Lee