ABSTRACT
Vehicle-to-Vehicle (V2V) and Vehicle-to- Infrastructure (V2I) networks are ephemeral, short-duration wireless networks that have the potential to improve the overall driving experience through the exchange of information between vehicles. V2V and V2I networks operate primarily by distributing real-time incident reports regarding potential traffic problems such as traffic jams, accidents, bad roads and so on to other vehicles in their vicinity over a multi-hop network. However, given the presence of malicious entities, blindly trusting such incident reports (even the one received through a cryptographically secure channel) can lead to undesirable consequences.
In this paper, we propose an approach to determine the likelihood of the accuracy of V2V incident reports based on the trustworthiness of the report originator and those vehicles that forward it. The proposed approach takes advantage of existing road-side units (RSU) based V2I communication infrastructure deployed and managed by central traffic authorities, which can be used to collect vehicle behavior information in a crowd-sourced fashion for constructing a more comprehensive view of vehicle trustworthiness. For validating our scheme, we implemented a V2V/V2I trust simulator by extending an existing V2V simulator with trust management capabilities. Preliminary analysis of the model shows promising results. By combining our trust modeling technique with a threshold-based decision strategy, we observed on average 85% accuracy.
RELATED WORK
Trust Management is a very broad field of research. An overview of general trust management approaches. It is important to note that for different application domains, trust management approaches are often highly customized to address application-specific requirements or constraints. As observed only a few approaches have been proposed in the literature to address trust issues in vehicular networks.
Some of the prominent approaches for V2V trust are, which focus on using local information available from the vehicles in the vicinity and simple consensus schemes to decide whether to trust received messages over the V2V network. We believe this provides an inherently myopic world-view and therefore is ill-suited for making good trust decisions.
SYSTEM MODEL AND PROBLEM STATEMENT
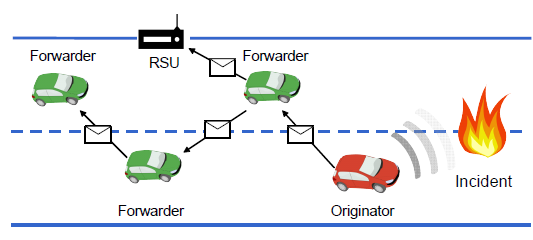
Fig. 1. Example Scenario of V2V-based Incident Report.
An simple scenario of the incident report generation and usage is illustrate in Figure 1. A vehicle driving on the road detects the occurrence of one or more incidents and automatically generates and forwards an incident report to other vehicles within its V2V communication range. The incident report message contains the description of the incident (e.g., time, location, severity level, etc.) to informs other vehicles.
TRUST MODEL
The key idea proposed in this paper is to construct a trust model for each vehicle participating (i.e., originating and forwarding) the V2V-based incident report propagation. This trust model is designed to compute a trust score that represents the likelihood that a vehicle originates or forwards accurate incident reports to other vehicles.
In this section, we provide an overview of the main elements of this trust model including our assumptions about the overall system, behavior exhibited by the vehicles and the trust modeling process. Please note that, in this work, we assume that all messages exchanged over the V2V and V2I network are cryptographically protected. The focus of this work is therefore solely on computing effective trust score for the vehicles.
V2V/V2I TRUST SIMULATOR
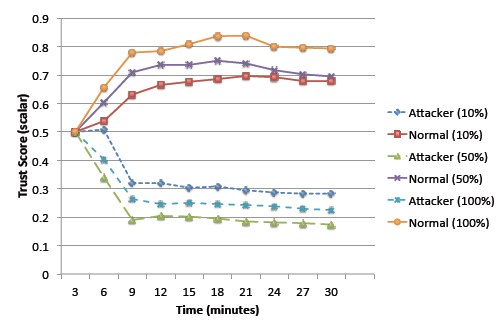
Fig. 3. Average Trust Score trend for vehicles with attackers and normal role at various percentages of incident report feedback.
Seeing the dearth of platforms available for simulating trust in V2V networks, we decided to build a V2V/V2I trust simulator. In this regard, we considerably extended an open source hybrid-network simulator called Groove Net with trust modeling capabilities. The screen-shot of our simulation system is shown in 2. In the simulator Vehicle is the principal entity in the simulator (shown as color circles in Figure 2).
PRELIMINARY EVALUATION
In order to validate our approach setup, we set up a simulation scenario with 70 vehicles in total using the map of New York city. We have 50 vehicles with normal role type, 10 vehicles with attacker role, and 10 with authority role. For attacker vehicles, the frequency of sending incorrect incident reports was set to 30 seconds/message. Normal vehicles only accepted and forward a received incident report if the trust-score of the originator is greater at least 0.7 (i.e., tthreshold = 0:7).
Further, any incident report forwarded by a user has an endorsement opinion associated with it, which is computed as AV Gtmax *tmax. Here, AV Gtmax is the average endorsement opinion expressed by vehicles with the highest trust score (tmax) among the originator and forwarders of the incident report. Authority vehicles are always assigned with the highest trust score set to 1 by the central authority. Further, they only accept and forward messages from other authority vehicles with an endorsement opinion of 1.
CONCLUSION
In this paper, we proposed an trust-based approach to determine the likelihood of information accuracy under V2V based incident report setting. By taking advantage of V2I channels between vehicles and central traffic authorities, we can construct a global view of individual vehicles trustworthiness in a crowd-sourced fashion, which overcomes the lack of vehicle behavior information due to the inherent ephemeral nature of vehicular networks.We also significantly extended an existing simulation platform with trust modeling capabilities to validate our approach.
Our preliminary evaluation shows promising result on the effectiveness of the proposed approach. In the future, there are three directions that we would like to explore: (1) we plan on using our new simulator for a more thorough analysis of the proposed approach and compare the proposed approach with existing trust management proposals for vehicular networks; (2) we would like to improve of the communication overhead, the impact of unreliable communication channel, and the cost of infrastructure deployment; (3) we would like to further study the trade-off of security and privacy issues introduced by using unique identifiers and PKIs.
Source: University of Pennsylvania
Authors: Cong Liao | Jian Chang | Insup Lee | Krishna K. Venkatasubramanian