ABSTRACT
As we get into the Internet of Things era, security and privacy concerns remain as the main obstacles in the development of innovative and valuable services to be exploited by society. Given the Machine-to-Machine (M2M) nature of these emerging scenarios, the application of current privacy-friendly technologies needs to be reconsidered and adapted to be deployed in such global ecosystem.
This work proposes different privacy-preserving mechanisms through the application of anonymous credential systems and certificateless public key cryptography. The resulting alternatives are intended to enable an anonymous and accountable access control approach to be deployed on large-scale scenarios, such as Smart Cities. Furthermore, the proposed mechanisms have been deployed on constrained devices, in order to assess their suitability for a secure and privacy-preserving M2M-enabled Internet of Things.
RELATED WORK AND BACKGROUND
The realization of the IoT ecosystem imposes significant restrictions on security and privacy, since physical objects are being seamlessly integrated into the Internet infrastructure, through the use of different wireless communication technologies. In particular, IoT scenarios are intended to manage particularly sensitive data, and consequently, any information leakage could seriously damage the user privacy.
This problem is aggravated in the IoT, since any smart object will be able to create new information and communicate it to any other entity. In the current Internet, identity management has been traditionally addressed by using well-known technologies, such as the Security Assertion Markup Languaje (SAML), OpenID or WS-Federation. In these mechanisms, an identity provider (IdP) entity is usually in charge of creating on-demand access token, in order to enable a secure communication between two entities.
- Related Work
- Preliminaries
SECURITY FRAMEWORK FOR THE IOT
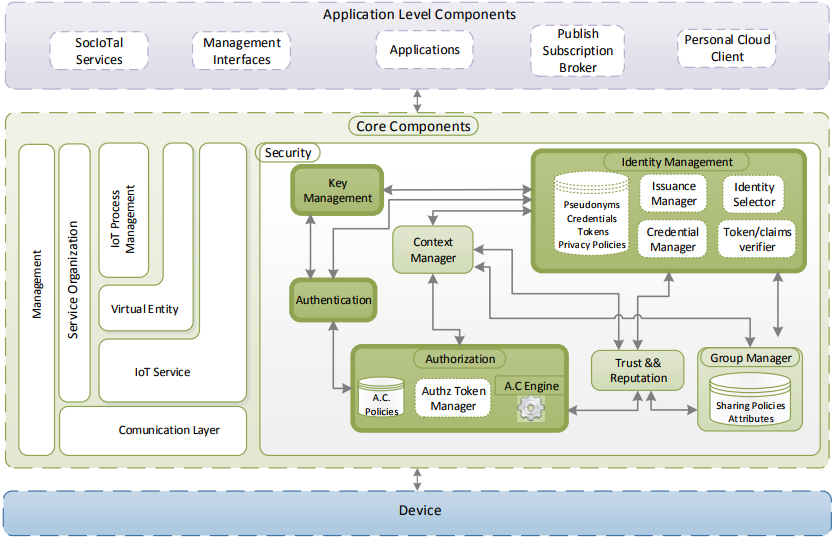
Figure 1. Architectural Reference Model (ARM)-based Security Framework for the Internet of Things (IoT)
However, security and privacy concerns are not the main focus of such architectures. In contrast, our ARM-compliant security framework addresses these requirements by instantiating and extending the security functional group of ARM, which promotes its applicability and interoperability in a wide range of IoT scenarios, in which security and privacy are required. Figure 1 shows our ARM-compliant framework, in which we highlight the main components that are addressed in this work.
PRIVACY-PRESERVING DCAPBAC ALTERNATIVES
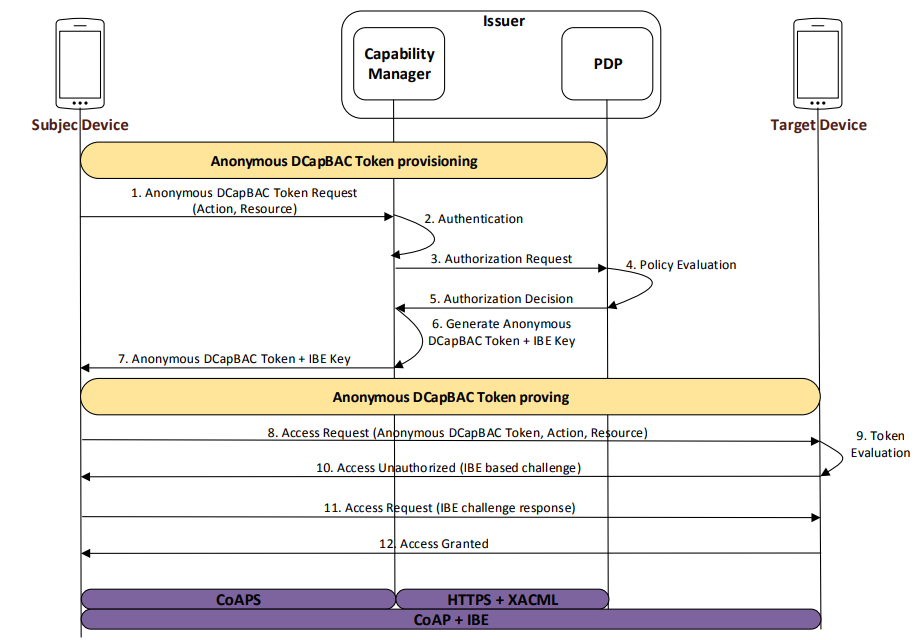
Figure 3 shows the main interactions of the IBE-based Anonymous DCapBAC approach. Firstly, during the provisioning stage (1–7 messages), the Subject entity requests an Anonymous DCapBAC Token to the Capability Manager by using CoAP, and specifying the action and the target resource for which it requests such credential. However, before sending this request, a secure channel is established between both entities through DTLS with certificate-based mutual authentication.
Specifically, we assume that the certificate of the Subject entity contains a set of identity attributes (e.g., manufacturer or device class), as part of the subject Directory Attributes extension within an X.509 certificate. Optionally, attribute certificates could be employed together identity certificates for the token generation stage, including additional attributes for authorization purposes. These attributes, along with the action and resource specified in the CoAP request, are used by the Capability Manager to build a XACML request, which is sent to the PDP within the body of an HTTP request.
EVALUATION RESULTS
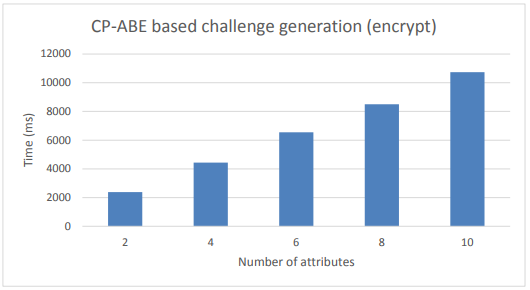
Figure 8. CP-ABE based Anonymous DCapBAC. Challenge generation performance
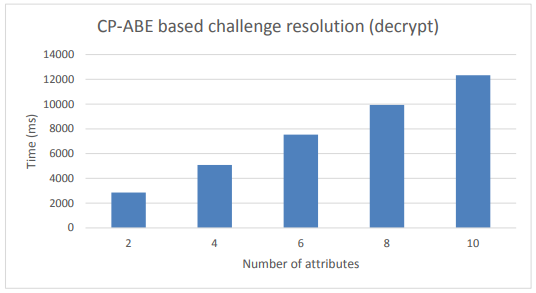
Figure 9. CP-ABE based Anonymous DCapBAC. Challenge resolution performance
Figure 8 shows the performance results for the challenge generation process, while the values of the resolution process are shown in Figure 9. These results were obtained by modifying the number of attributes defined in the access policy from 1–10, since we consider this range expressive enough for most scenarios and use cases.
Furthermore, at this point, it should be pointed out two aspects of this evaluation. On the one hand, these values were achieved by considering an 80-bits security level (i.e.,|p| = 512 and |q| = 160), which is suitable for scenarios with medium security requirements.
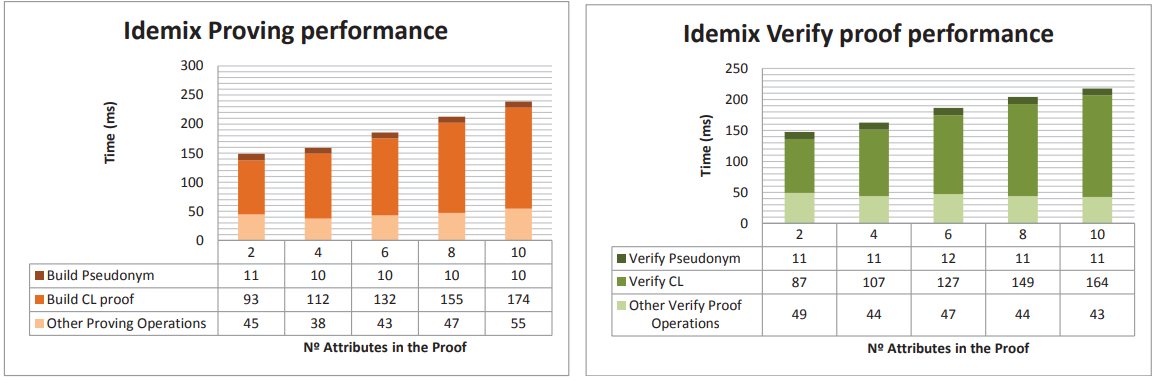
On the other hand, the Verify Proof operation, which is carried out by the target device, is shown in the right chart of the Figure 10. The total time required during the proof verify task is split again to show independently the time required to verify the pseudonym and the CL signature. As it was predictable, the times increases as the amount of attributes in the proof is higher.
DISCUSSION
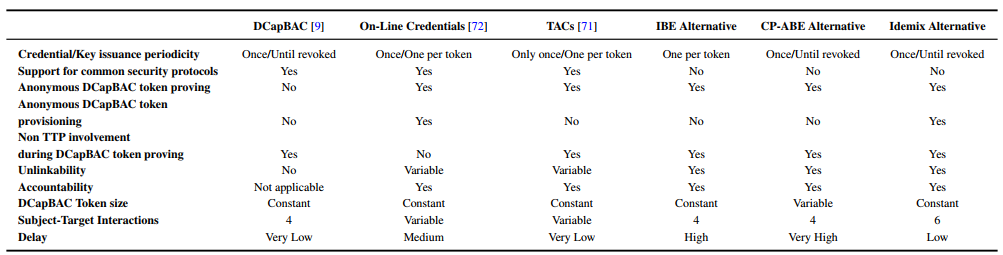
Table 1 shows the analysis of these alternatives regarding privacy features and practicality aspects, which must be considered for a real deployment on IoT environments. The Credential/Key issuance periodicity aspect is related to the management of cryptographic material that is used to demonstrate the possession of an Anonymous DCapBAC token in a privacy-preserving way. However, it should be pointed out that the tokens themselves could be also generated according to a different issuance periodicity.
CONCLUSIONS
The realization of a secure and privacy-preserving M2M-enabled IoT must face serious technical and social challenges. Several aspects related to scalability, dynamism, heterogeneity or usability need to be addressed in the design of new, valuable and secure services to be exploited by society. Under the main foundations of certificateless public key cryptography and anonymous credential systems, we have presented the design of three different mechanisms to enable an anonymous and traceable access control approach. Furthermore, these mechanisms have been developed and evaluated in order to assess their suitability for a real deployment on constrained device.
According to the presented results and the security discussion, the proposed Idemix-based access control alternative provides advanced privacy features, as well as reasonable performance results, making it a promising approach to be considered on real scenarios. Moreover, its high level of flexibility and scalability, future fork is focused on the design and evaluation of secure and privacy-preserving group communication mechanisms based on certificateless public key cryptography.
Source: University of Murcia
Authors: José L. Hernández-Ramos | Jorge Bernal Bernabe | M.Victoria Moreno | Antonio F.Skarmeta
>> Latest 50+ IoT based Security Projects for Engineering Students
>> 200+ IoT Led Projects for Final Year Students
>> IoT Environmental Monitoring System for Smart Cities Projects for Students