ABSTRACT
The Internet of Things (IoT), which can be regarded as an enhanced version of machine-to-machine communication technology, was proposed to realize intelligent thing-to-thing communications by utilizing the Internet connectivity. In the IoT, “things” are generally heterogeneous and resource constrained. In addition, such things are connected to each other over low-power and lossy networks. In this paper, we propose an inter-device authentication and session-key distribution system for devices with only encryption modules.
In the proposed system, unlike existing sensor-network environments where the key distribution center distributes the key, each sensor node is involved with the generation of session keys. In addition, in the proposed scheme, the performance is improved so that the authenticated device can calculate the session key in advance. The proposed mutual authentication and session-key distribution system can withstand replay attacks, man-in-the-middle attacks, and wiretapped secret-key attacks.
REVIEW OF SECURE IOT ENVIRONMENT
The IoT service middleware platform should satisfy the following requirements in order to provide the function of acquiring and analyzing sensor-network monitoring information or sensor data periodically and continuously in the links of multiple heterogeneous sensor networks for IoT application services.
- User Authentication and Authorization
- Platform Session Management
- Service Message/Notification
- Sensor Network Monitoring and Control
- Sensor Data Acquisition/Processing
- Authentication and Session-Key Distribution between IoT Devices
- Lightweight Security Technology for IoT Environments
PROPOSED SECURITY SCHEME
In this paper, we propose the categorization of resource-limited sensors in the WoT environment proposed by the Lightweight Implementation Guidance (LWIG) working group as Class 0 super-light sensors and Class 1 or above sensors. Further, we propose the appropriate application of the authentication method and the session-key sharing method for the performance of each group of sensors. The parameters used in the proposed system are as follows:
– I is the authentication initiator.
– R is the responder to the message sent by the authentication initiator.
– r1 and r2 are random nonce values.
– kIR is the key that is securely shared in advance between the authenticator and the responder.
– sk is the session key that is shared between the authenticator and the responder.
- Symmetric-Key-Based Authentication and Session-Key Agreement Scheme
- Hash-Based Authentication and Session-Key Agreement Scheme
- Comparative Analysis
- Security Analysis of Proposed Scheme
SERVICE FLOW OF IOT SERVICE MIDDLEWARE PLATFORM
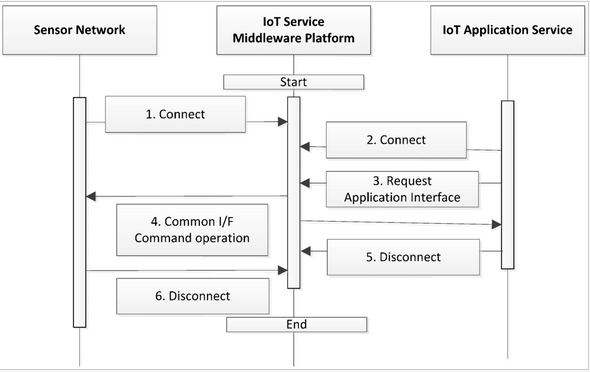
The flow of platform operation is shown in Figure 1 above. The platform enters the operational state after the initial actuation, and a link is then established to the sensor networks and application services. Multiple sensor networks are linked by the connection requests in the operational state of the platform, and the application services are then also linked to the platform in its operational state.
The platform linked to the sensor networks processes the commands continuously according to the common-interface standard based on service requests obtained by application services, and each application service performs its actions using the application interface with the platform. Connections between the applications and sensor networks are possible. Finally, the platform stops functioning as a platform in the finish stage (Figure 1).
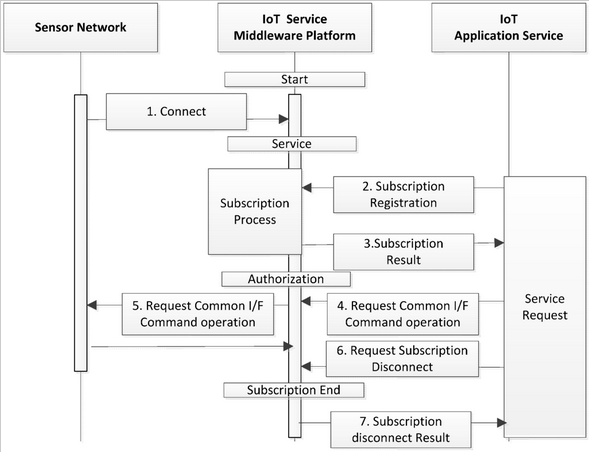
The flows of the sensor-network monitoring and control are shown in Figure 4. The sensor networks linked to the platform transmit the monitoring information periodically via the common interface of the sensor network. The platform dynamically updates the monitoring information of the multiple sensor networks that are linked to the platform, and maintains them for use in the related application or platform. The USN application service obtains the monitoring-state information from the platform in the form of a notification.
COMPARISON WITH RELATED WORK
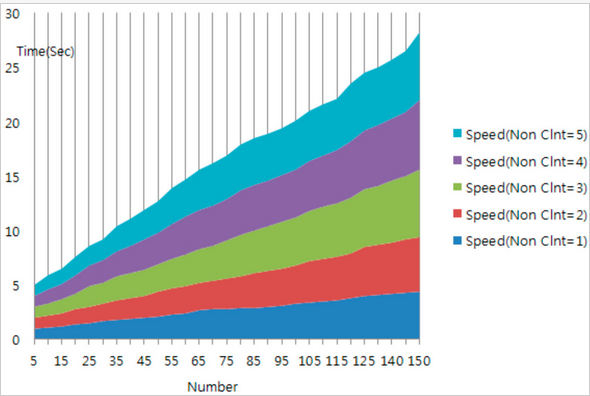
Figure 5. Simulation result for J-IoT middleware filtering
Figure 5 showed difference for 4s that compare average transfer time between client and mobile IoT middleware of middleware filtering and unfiltering by network. Generally, as the tag number increased, showed phenomenon that increase until 4s.
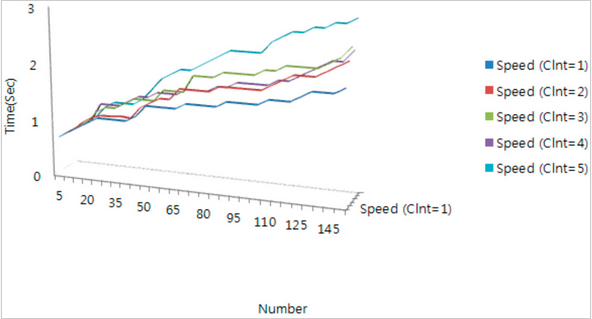
Figure 6. Simulation result for mobile IoT middleware non-filtering
Figure 6 shows the average transmission time with increasing tag number in a non-filtering protocol environment. As the tag number increases, we observe that the average transfer time generally increases. Moreover, the average transfer time increases rapidly in the case where the tag number is greater than 45.
Therefore, about 40 IoT devices can be simultaneously processed stably by a PC in a test bed environment. When we compare the filtering time and protocol time, the time of mobile IoT middleware platform’s filtering module is occupying and shows the importance of the signature module for about 32% of the entire protocol time.
CONCLUSIONS
The IoT, which can be regarded as an enhanced version of M2M communication technology, was proposed to enable intelligent thing-to-thing communications by utilizing Internet connectivity. In the IoT, “things” are generally heterogeneous and resource constrained. In addition, such things are connected with each other over LLNs. In this paper, we focused only on inter-device authentication and the session-key distribution system for devices with only encryption modules.
In the proposed scheme, unlike existing sensor-network environments where the key distribution center distributes the key, each sensor node is involved with the generation of session keys. In the scheme, the performance is improved so that the authenticated device can calculate the session key in advance. The proposed mutual authentication and session key distribution system can withstand replay attacks, man-in-the-middle attacks and wiretapped secret-key attacks.
However, the proposed system assumes that the devices involved securely share kIR. If kIR is compromised, there is a limit to the security that can be guaranteed by the proposed system. Like many existing proposed systems using preset secret keys, in this paper, the proposed system assumes secure channels and storage methods. However, further research is required to realize the secure sharing of kIR.
Source: Jeju National University
Authors: Namje Park | Namhi Kang
>> Latest 50+ IoT based Security Projects for Engineering Students
>> IoT based Real-Time Projects for B.E/B.Tech Students